DNS Detection Techniques
the network is not only the organization’s critical asset, but also adversaries’s one. they will need to use the network either for moving laterally or vertically towards the C2 server.
Almost every connection uses DNS now, they can sometimes even tell the story of what was accessed.
if you find 10.10.4.6 requesting the ip for www.google.com it means that probably www.google.com was accessed, thats a powerful concept. Request thus Access.
For that, in this article i will be discussing simple Detection Techniques based on DNS.
Ah, before that. quick tip, try to enrich your dns logs with domain length, domain age, frequency score (freq.py will see it later), geo information (MaxMind) and Tagging (internal/external domain, top-1m)
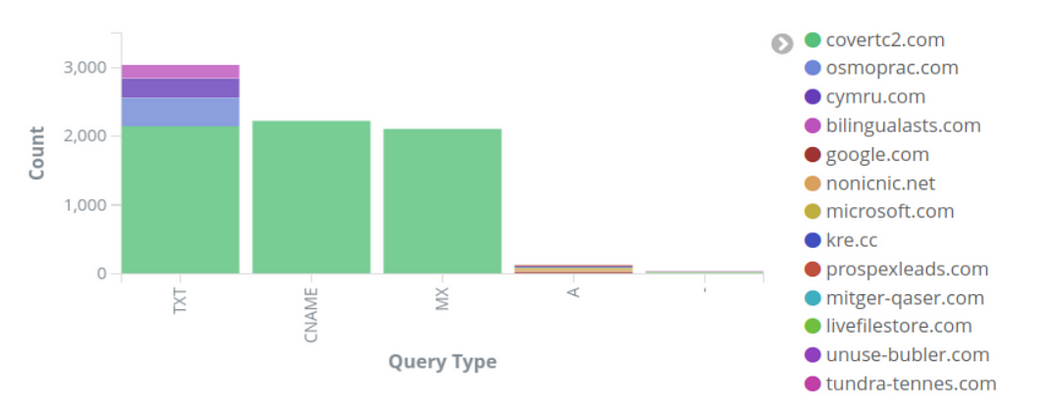
Query Type Analysis
how many queries by query type? for example, a high number of queries for rare records types like TXT or SRV might indicate data exfiltration or DNS based C2.
How to?
well, Collect the log first right? :D . either from tap/mirror sensors like zeek or from endpoint. You need data before using data :)
use visualization, its ur ally. this an example :
DNS Fuzzy domain matching ( also called levenshtein distance search)
Attackers may use typo squatting, registering domains similar to legitimate ones to trick users. fuzzy matching helps identify such domains. our brain is really good as noise suppression so you can easily miss such attack.
Example: Detecting a query for “goggle.com” instead of “google.com” could indicate a typosquatting
DNS Sinkhole Detection
Sinkholing is a technique where known malicious domains are redirected to a non-existent or controlled IP address. Analyzing DNS requests for known sinkholed domains can identify infected hosts within a network.
Example: If a known malicious domain “malware.example.com” is sinkholed to 0.0.0.0, and a host on your network repeatedly tries to resolve this domain, it may indicate an infection
Frequency Analysis
most of the domain names in the internet are already random, so entropy won’t be really helpful. what can be helpful is frequency of each char.
you can check this repo by Mark Baggett, which provide you with a tool that can use frequency analysis to score domains, you feed it a list of normal domains ( like top 1m) and it will generate based-on scores. like how probable is to find M followed be a.. marco.
https://github.com/MarkBaggett/freq
GeoIP Correlation
Imagine if you need to allow list Microsoft ips, they are millions. do you want to allow million ips or just allow the ASN?
furthermore, Identifying requests to unusual geographic locations or connections originating from suspicious ASNs (like those associated with known botnets) can flag potential threats.
MaxMind Geo database can be used in this case.
Allow Listing
its not a detection technique by itself but can be used to filter the most used domains, Doesn’t mean they are a Known Good, but can be good for long tail analysis. for example using cisco umbrella top 1m to either totally filter them out in aggregation phase or add a tag on each domain that belong to.
